HOW TO REPORT HACKERS
Stopping
hackers can be very difficult sometimes seemingly
Reporting
hackers can sometimes be a little bit tricky. A lot of
Once
your system is connected to the Internet, some form of
What
do you do now that you know that someone is attempting
(Consult
your firewall program documentation for instructions on
Once
you have identified how many times the person has
·
Write down the IP address you were
given by Black Ice and
Type
the following at the DOS prompt.
This
will give you a listing of all active connections to your Active
Connections
·
After typing in the IP Address Click
on Ping indicated
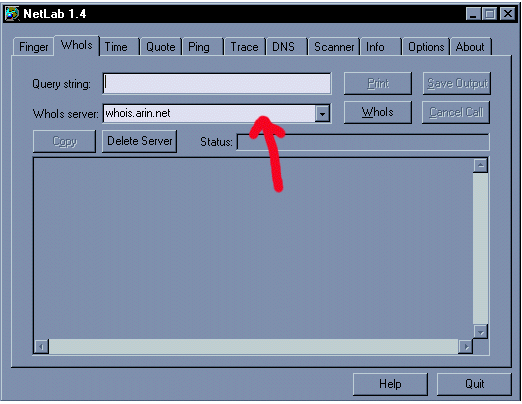
Once
you’ve typed in the IP address in Query String Click on the
is coming from you can forward the appropriate information to
the right people. Let’s
recap our procedure in a step-by-step format.
Once
you’ve done the steps above you will need to send the
impossible.
I believe however if you use the right types of
programs
combined with self-education on how hackers think,
you
can make your computer much safer.
users
never report hack attempts. Simply because they just
don’t
care or believe that the “hacker” knows he can’t get into
their
system. There is also the reason that users just don’t know
what
steps to take once they realize their system is being
attacked.
system
attack will eventually hit your computer. Most of the
times
these attacks will be completely random. While not every
single
attack ever made should be reported, repetitious attacks
should.
Repeated attacks from the same person/IP address
should
always be reported. This is a clear indication that
someone
is trying to gain access to your computer.
will
be able to see the IP address of the person attempting to
break
into your system.
to
hack into your computer?
Before
you can do anything you will require some utilities. I
recommend
getting the following program.
·
NetLab
Netlab
has a variety of utilities combined into one easy to use
application.
You
can obtain a copy of Netlab from:
After
obtaining a copy of NetLab and installing it you’ll be ready.
I
find the best procedure for this is to begin by identifying how
many
times this “individual” has attempted to hack into your
system,
and at what times.
where
to locate the number of attacks originating from an IP
address.)
attempted
to gain access and at what time the most recent
attack
was, it is a wise idea to check if they actually got through.
To
check what is currently connected to your computer, do the
following:
or Lockdown 2000
·
Click Start
·
Go to Run
·
Type in Command and hit Enter
This
will bring you to your DOS prompt again.
·
Netstat
computer
and it will look something like this.
Protocol Local Address Foreign Address State
TCP COMP: 0000 10.0.0.1 : 0000 ESTABLISHED
TCP COMP:2020 10.0.0.5 : 1010 ESTABLISHED
TCP COMP:9090 10.0.0.3 : 1918 ESTABLISHED
Your
information will have different numbers. I used the IP
address
10.0.0.x for demonstration purposes only.
If
your attacker is connected to your computer, you will see his IP
address
in this listing. Compare this listing to the IP address you
have
written down.
In
the table above you will see numbers after a (:)
For
example: COMP: 2020
The
2020 represents the port number that the Foreign computer
is
connected to on your computer.
Using
our example let’s take a look at the second row. This
shows
us that someone is connected to our computer on port
(2020)
from the IP address 10.0.0.5.
Once
you have assessed that the “hacker” was unsuccessful in
his
attempts to hack into your computer, you can proceed to
gather
information to report the attack.
Start
up NetLab
·
Type in the IP Address in the
indicated area below
Below
At
this point you will see one of two results. You will see a
response
indicating either the person is online or you will see no
response
indicating they are offline. We do this to check if the
person
is still connected.
2:
The time it takes to ping the address.
The
next step is to check who the IP address belongs to. You can
do
this by using whois.arin.net on the person’s IP address.

Whois button. You will
then see who the IP address belongs to.
This
will reveal who the “hackers” internet service provider is.
This
is very important, if you can figure out where your attacker
is coming from you can forward the appropriate information to
the right people.
A)
Drop to the DOS prompt
B)
Run netstat to check if they got through
C)
Start Netlab and do a Ping Test to check if they are still
connected
D)
Do a Whois (Using the whois.arin.net) lookup
information
to your ISP and the attacker’s ISP. The goal is to
give
them as much information as you can about the attacker.
Both
firewall programs (Black Ice Defender) and (Lockdown
2000)
create log files of each attack. Copy the information along
with
your own test and include the times of each attack into an
email
and send it to your ISP provider. Send a copy of that email
to
your attacker’s ISP provider also.
(Note:
You may need to call the attackers ISP provider in order to
get
the right Email Address. If the call will involve long distance
All
ISP providers have an Abuse department. They are
responsible
for dealing with such issues. If you send the email to
the
support department of the “hackers” ISP they will forward it
to
the correct division.
It
is your responsibility to report any attacks being made against
your
computer. I encourage you to take an active part in
reporting
repeated attacks from the same IP address against
your
computer, as these are clear indications of someone
targeting
you.
It
may be that you have something they are interested in, or
perhaps
your system has been compromised prior to your
realization,
and with the installation of the firewall program you
are
now blocking their attacks. Whatever the reason now thatyou are aware your goal
is to
protect your privacy.





No comments:
Post a Comment